
Shardeum Incident Report: Cycle Exploit Postmortem
Learn how the Shardeum team swiftly responded to a cycle exploit, issued a patch, and burned all returned SHM to protect the...

Learn how the Shardeum team swiftly responded to a cycle exploit, issued a patch, and burned all returned SHM to protect the...
A recent incident on the Shardeum network saw the creation of ~500K SHM as a faulty staking reward. The Shardeum team swiftly identified and resolved the issue, and all of the created SHM was voluntarily returned to the Foundation wallets. This post-mortem offers a detailed analysis of the event and outlines our proactive measures to fortify the network against future occurrences.
On 12th July 2025, our team was notified of a suspiciously high staking reward by a community member via our Discord server. The Shardeum team quickly swarmed on the problem and determined this was the result of a deliberate attack on the Shardeum network. If you are a node operator, you may have noticed changes in the behavior of stakelock over the July 12th weekend. The Shardeum team temporarily increased the stakelock time in an effort to prevent any further malicious activity.
This turned out to not be necessary, but we were taking every precaution to prevent further damage. The attack stemmed from a simple but critical flaw in our validator software – an “off-by-one” error in our certificate validation logic that survived multiple rounds of testing, refactors, and auditing. While the vulnerable code was relatively simple, the attack required to exploit this vulnerability through multiple layers of security checks was sophisticated. The end result of this attack was tricking the Shardeum network into thinking a single node had been active in the network since 2019, resulting in an improper credit of approximately 500K SHM during cycle 111165.
Our investigation confirms this appears to be an isolated incident, and we have found no evidence of further impact across the network’s history. We have already released a mandatory security patch, Validator v1.19.3, which corrects the underlying flaw and implements additional defensive checks.
The Shardeum network operates one “cycle” at a time. Each unique cycle has a “cycle record” that details the state of the L1 at that specific point in time. This includes things like the current cycle number, which validators are active/joining/lost, which archivers are active, the hash of the previous cycle record (called the “cycle marker”), and other things. This information is consensed upon by the network before being added to the chain as a signed “cycle certificate”.
The sharded nature of the network requires multiple candidate cycle certificates to be considered before one is deterministically picked. Each of these candidate cycle certificates is cryptographically verified. That is to say: each candidate cycle certificate should be signed off on by active validators via power-rank consensus in the current cycle attesting to its accuracy. Before any new cycle certificate is even considered, it gets put in an array and every record is validated in this way. Here is the code that implements this critical check:
for (let i = 1; i < certs.length; i++) {
if (inpMarker !== certs[i].marker) {
return false
}
}TypeScript is a language that starts arrays at 0. If you can get your phony cycle certificate into the 0 element of the array, it gets to skip the marker validation step.
The Shardeum team’s initial suspicion was an issue with the staking reward mechanism. This prompted us to increase the stakelock time to prevent further reward calculation from occuring while we triaged the issue. As we further investigated and eventually found the issue, we took the following steps to ensure this was the first and only occurrence of this sort of attack:
1.19.3 and fixed the array-indexing problem. We have also greatly expanded our network monitoring to look for:
Shardeum is a community network and depends on the community for safety and security. If the attacker had reported this critical vulnerability to us rather than exploiting it on the live network, they would have been given our highest tier bounty reward. Therefore, if you identify a potential security issue, you have a few options to get our attention:
No action is needed. The issue was limited to validator reward accounting and did not impact user balances or transaction data.
As a validator, it’s important to ensure your node is running the latest patched version. Shardeum team will be monitoring the network for the next 1 to 2 days, after which community nodes will begin rotating into the active validator set. You can check if your validator is updated to the latest version in two ways:
On GUI
The latest version is shown right on the main dashboard under Version Info.
On CLI
Run these commands in your server terminal and look for shardeumVersion in the output. If it matches the latest version, your validator is updated
```bash
cd shardeum
./shell.sh
operator-cli status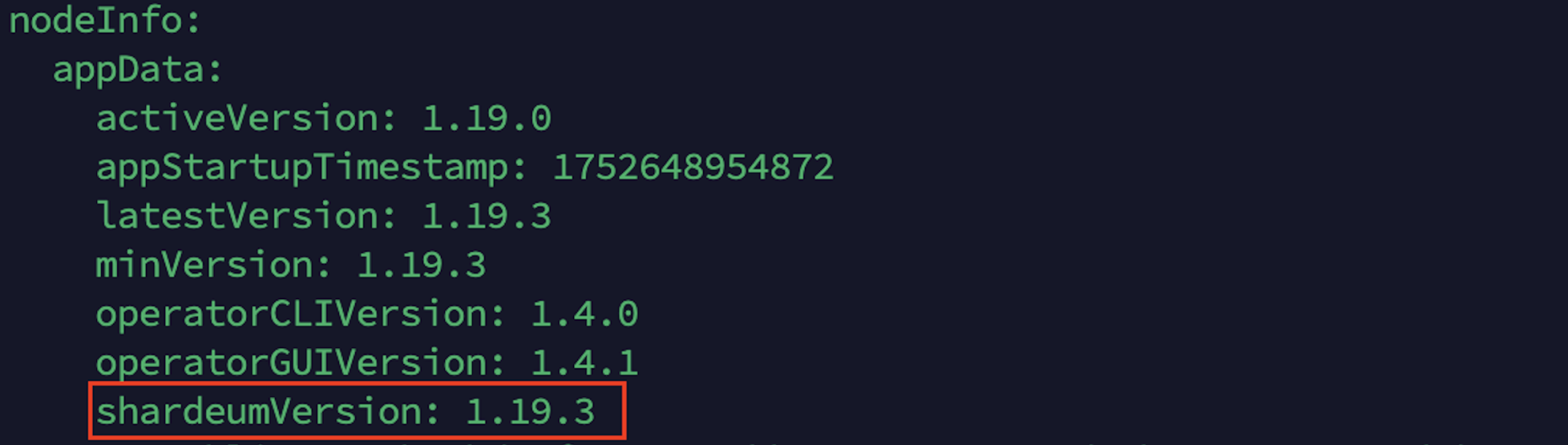
Huge thanks to the community member NoviceCrypto and others involved who reported and helped monitor the discrepancy quickly. Responsible reporting shortens response time and protects the network.
Updates: i) Details of the SHM burn, including the transaction hash and date, were appended on July 31, 2024. ii) Corrected the abnormal reward amount to 502,692.05 SHM (previously 502,694.51 SHM) and added the corresponding explorer link in the blog reflecting the accurate value.